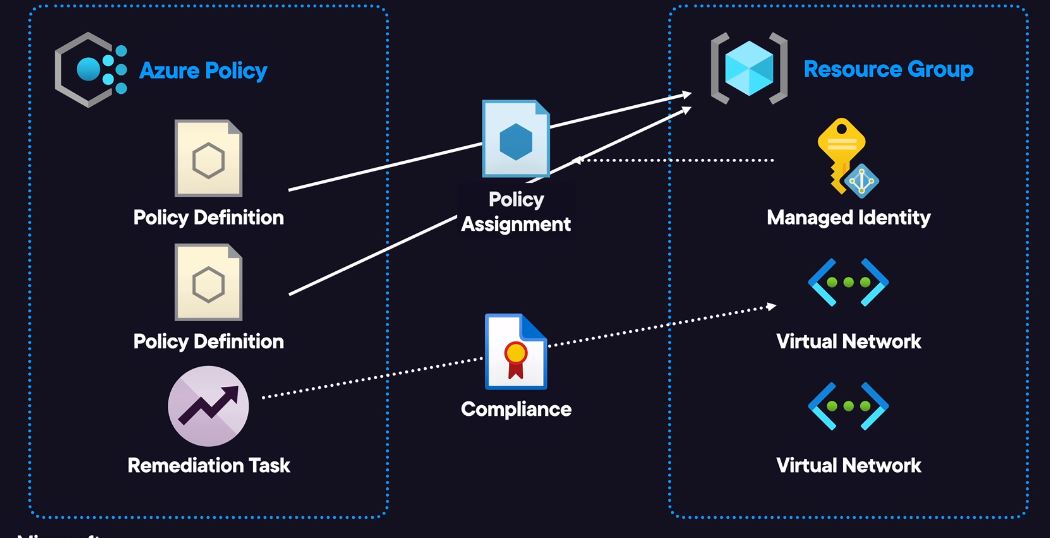
The task
I assumed the position of a security engineer tasked with ensuring compliance of Azure resources. Here are the following tasks.
- Ensure that Azure resources have a “Money allocation” tag associated with them so that chargebacks can be calculated on monthly Azure bills
Services used
- Azure Resource Group
- Azure policy
- Virtual Network
- Managed Identities
Steps to implement this:
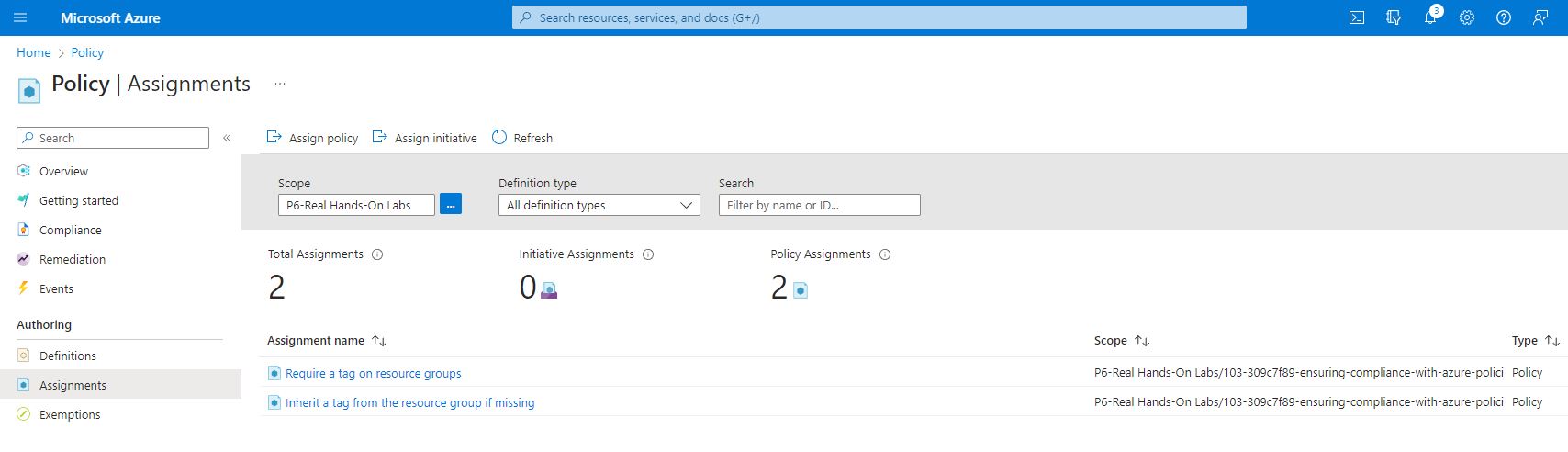
There are 2 policy definition for this lab.
The first policy definition is used to ensure that resources have acquired tag
The second policy definition is to ensure that any resources that are deployed without the required tag will inherit the tag from the parent resource group
NB: Second policy supports remediation, this means associating the existing managed identity with the policy assignment.
To test the result, I deployed another virtual network of the azure policy assignment.
To bring the existing virtual network into compliance, I created the remediation task that will use the managed identity associated with the policy assignment I created to remediate the existing virtual network.
- Assign Azure Policies:
- Assigned two built-in policy definitions :
- Require a tag on resource groups ( to ensure that all new resource groups has a cost allocation tag)
- Inherit a tag from the resource group if it is missing ( this will ensure that new non compliant resources will automatically inherit their cost allocation tag from their parent resource group).
- I used the remediation tags to bring any existing resources into compliance.
- Associate an existing managed identity with the policy assignment where it’s supported.
- Update and create resources
- To test the effect of Azure policy
- Created a cost allocation tag on the resources group to be inherited to the new non compliance resource group.
- Created a new virtual network (without providing the cost allocation tag to see the effect of the Azure policy assignment).
- Observed the results
- Checked for compliance on new and existing resources ( checked if the existing VNet has the required tags, if the new VNet has the required tags)
- Remediated Non Compliance resources
- By creating a remediation task to bring the existing resources into compliance
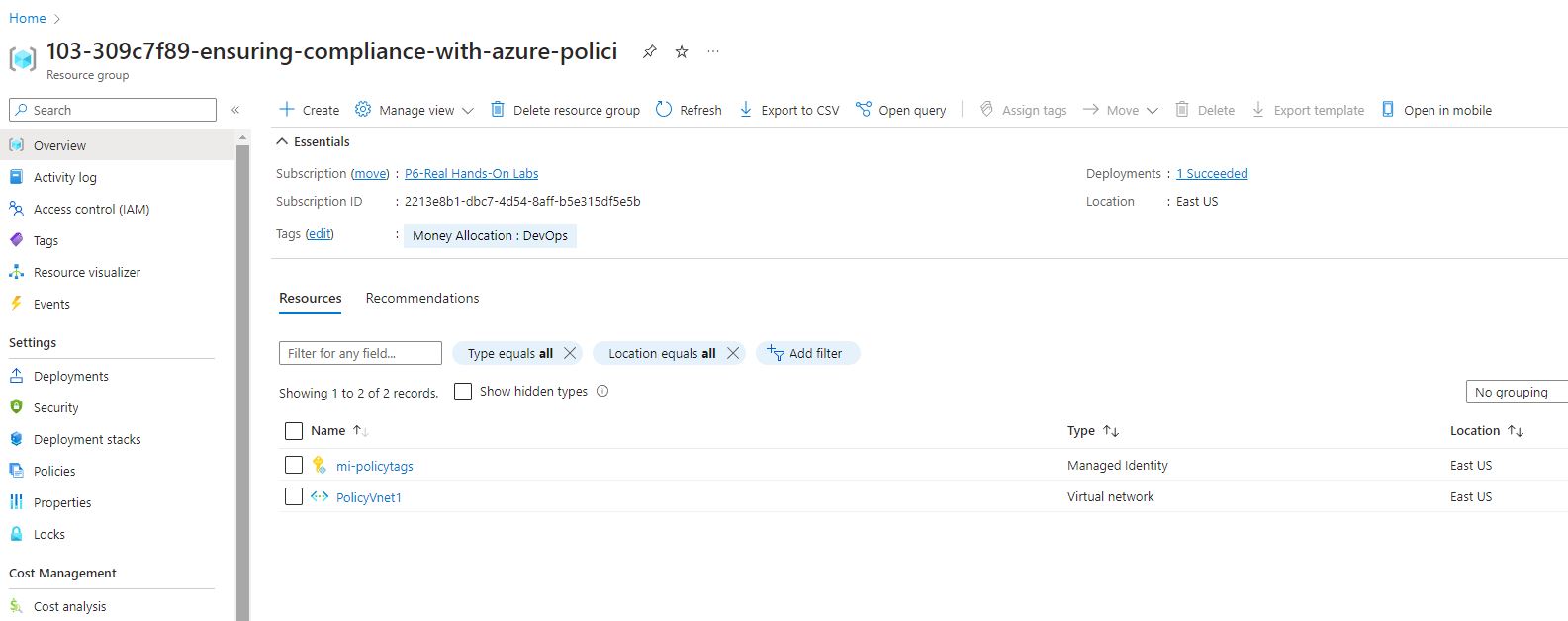
I ensured my resources used the same location (East US)
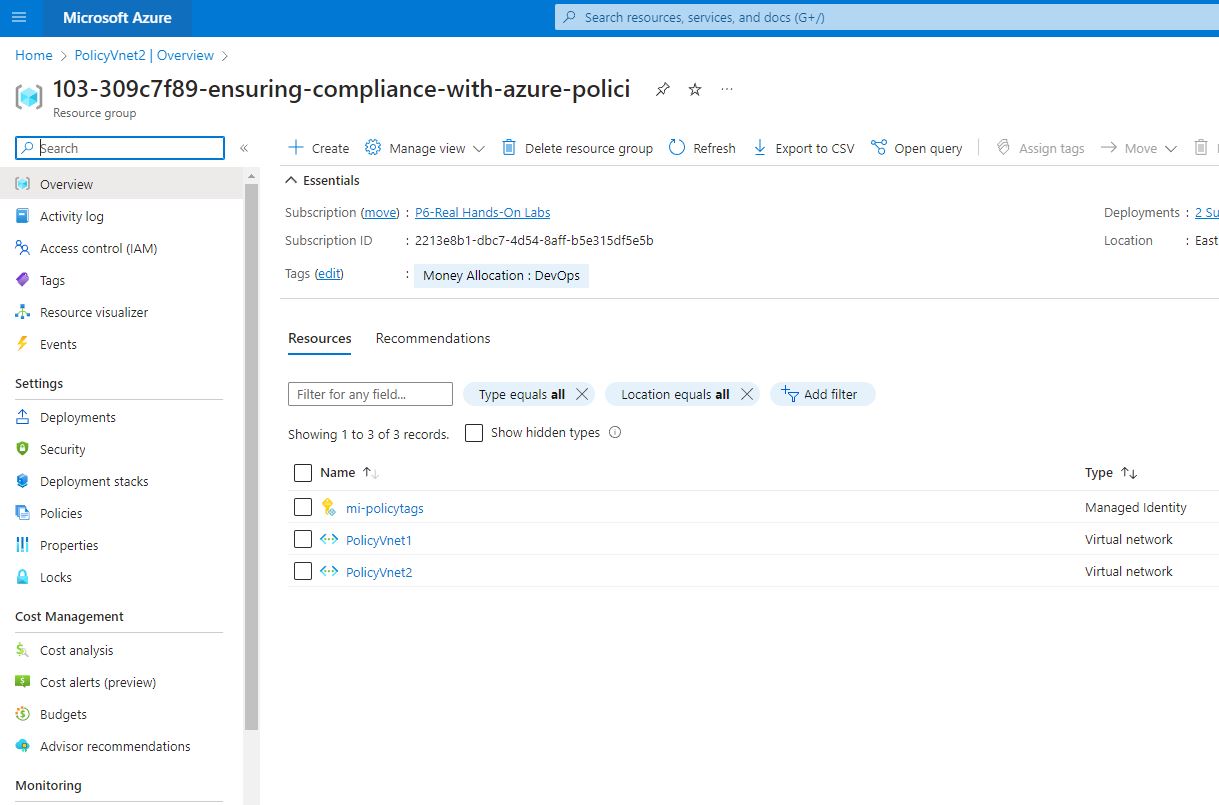
Here are some of the resources provisioned for this lab
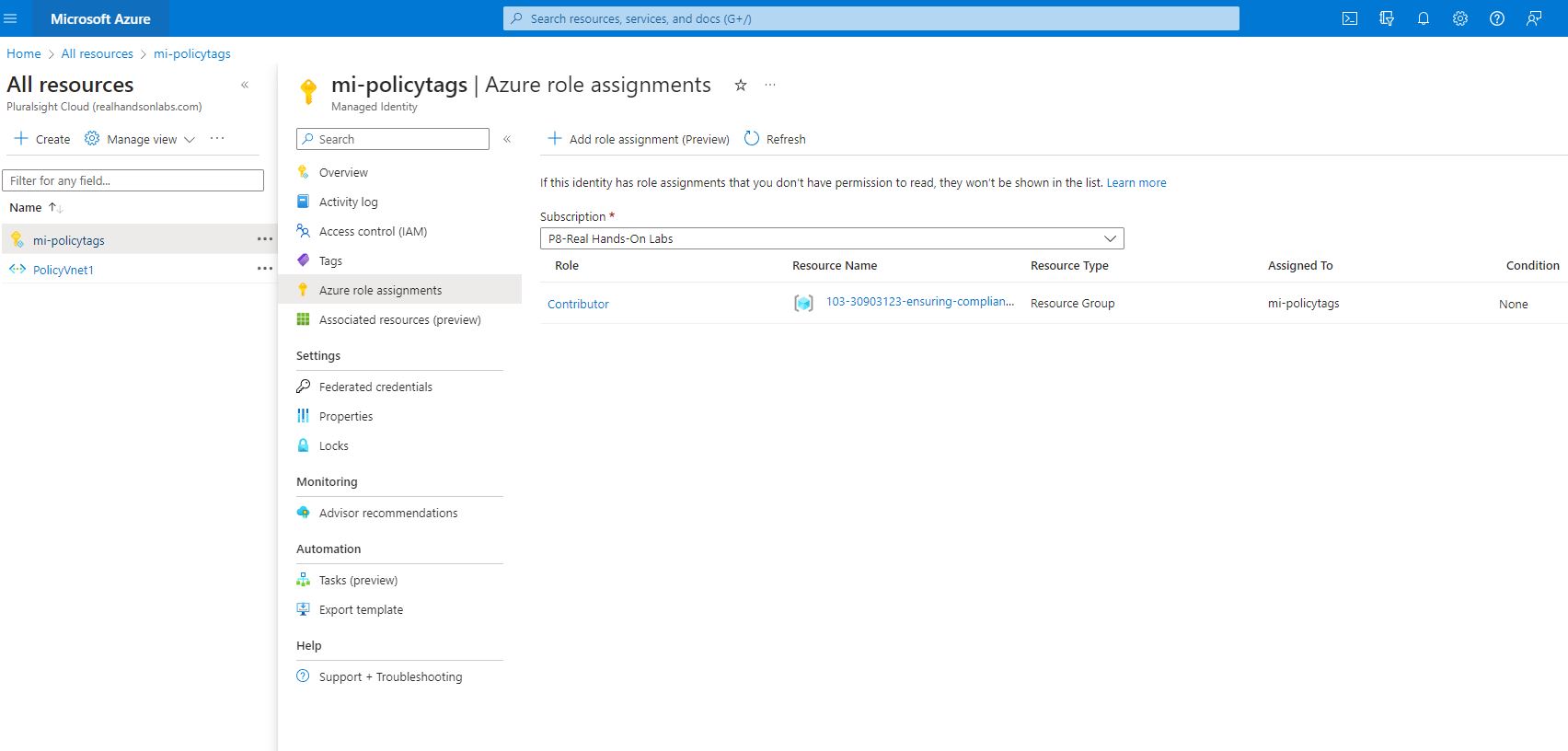
I dived into the Managed identity and looked at the Azure role assignments. As you it shows below, the managed identity has the contributor role, which is the required built in role for the remediation tags on the policy that I will be assigning in this lab going forward.
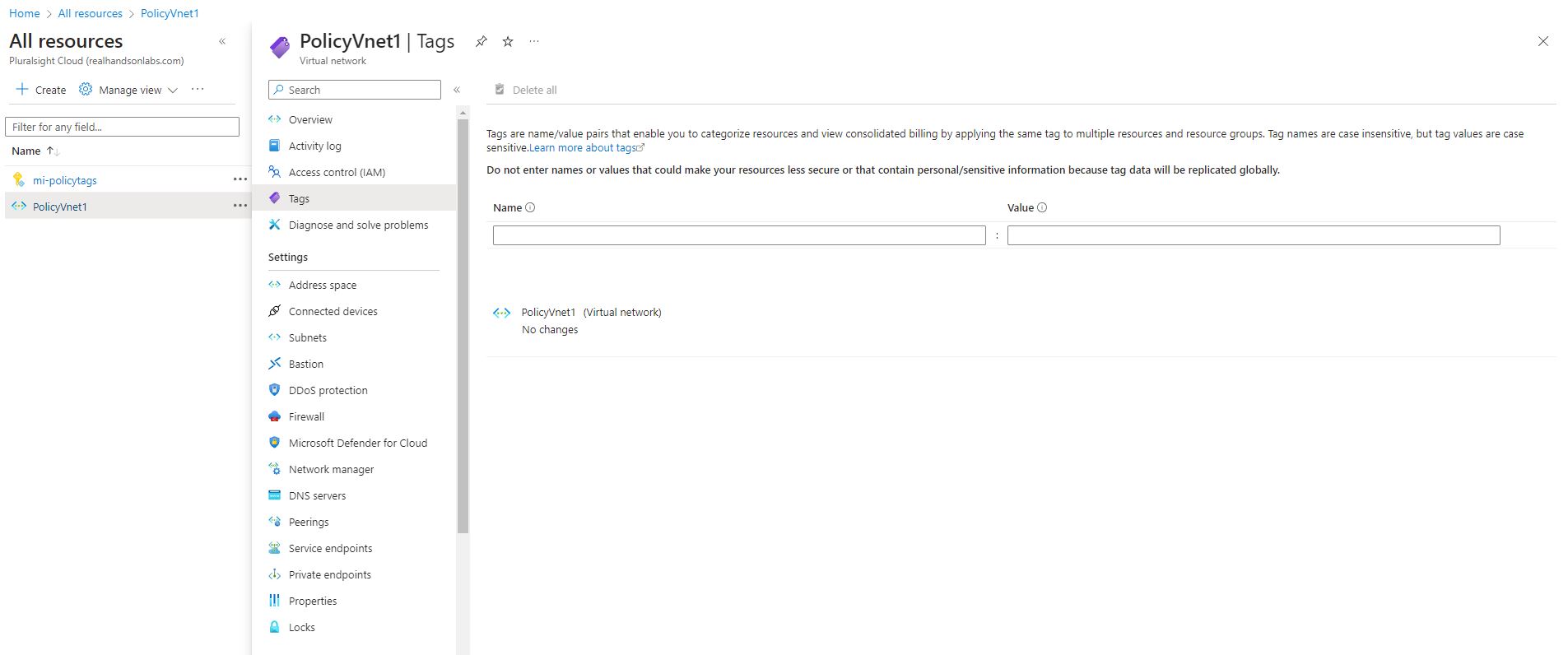
Also for the Virtual network, you can see below the existing virtual network (PolicyVnet1) has no tags associated with it.
To Start with the first objective which is to assign Azure policy
Selected the service on the portal called “policy” from the left hand pane selected assignment. Here the first policy to be assigned will require a tag on resource groups. The policy will ensure that all new resources groups created have the required tag so that another policy can inherit the tag from the resource group to the child resources.
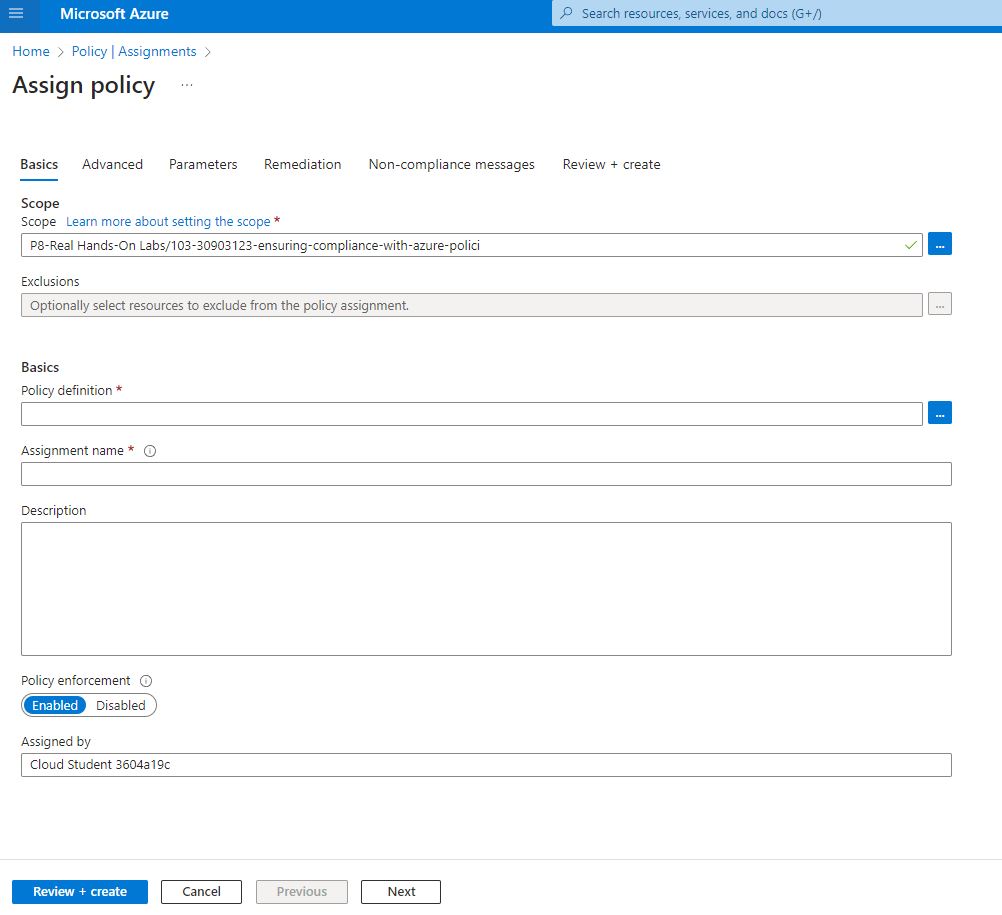
Selected the scope to the resource group.
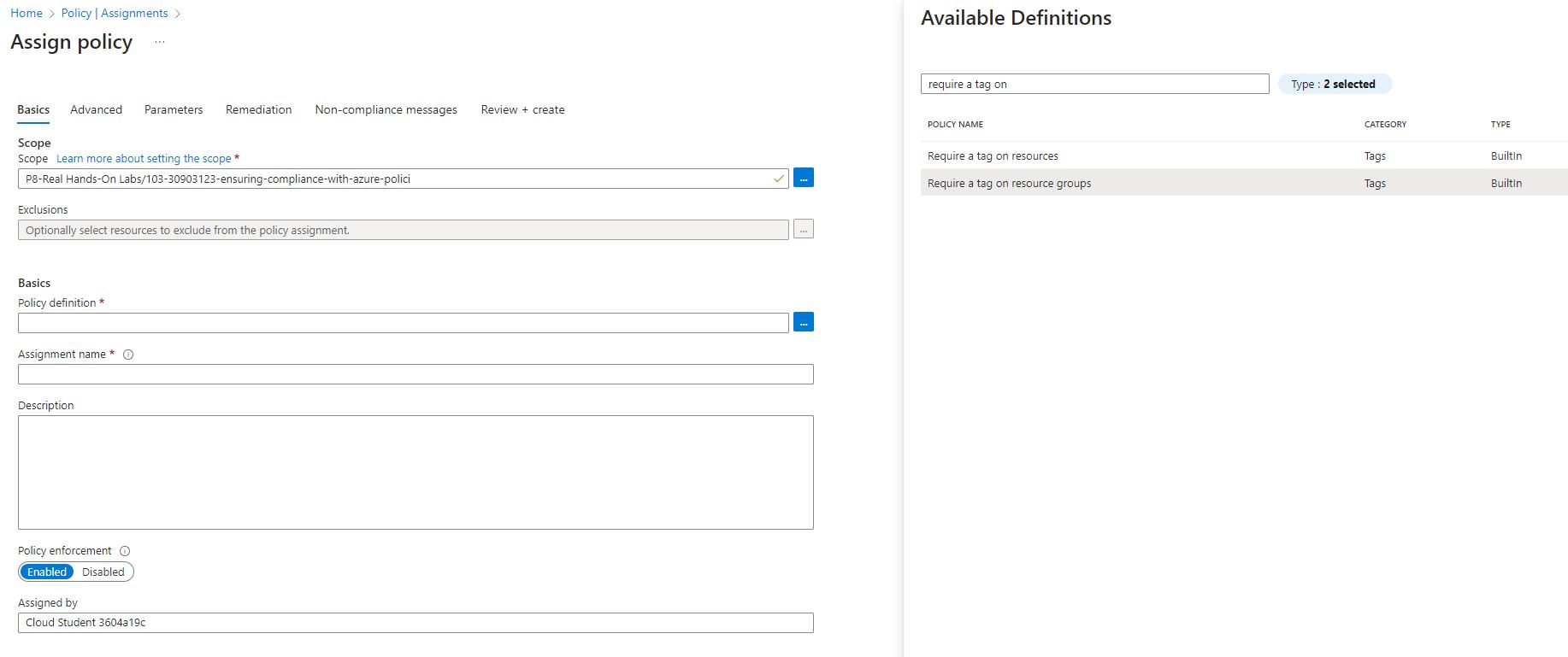
Choose the policy definition and search for required tag on ( require tag on resource groups)
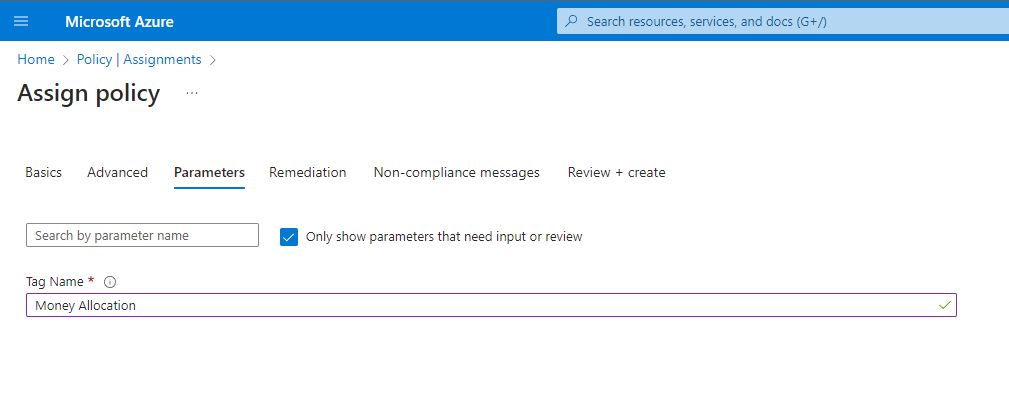
As the Advanced in not needed here, I jumped to parameters and provide the Tag name “Money Allocation”
Skipped the remediation as did not perform a remediation on this policy and jumped to Non-Compliance messages tab. Here I provided a helpful message that will remind people deploying Azure resources as to why this policy is enforced.
Helpful message” Resource Groups must have a money allocation tag for financial reporting and chargeback”
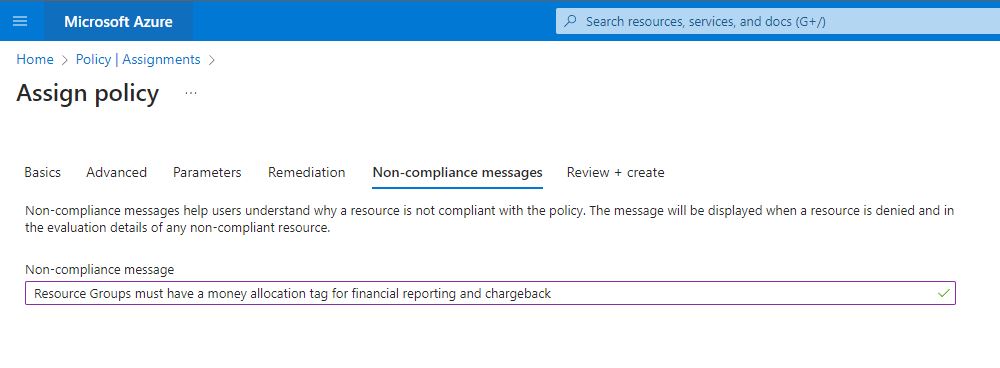
Then review and create
Created a second policy assigned which will have to copy or inherit a tag from a resource group to the child resources if it’s been admitted at the time of the deployment of that resource
Now following the same step as above, clicked on the assigned policy, selected the resource group for the lab from scope.
Selected the built in policy definition again, here I selected the “inherit a tag from the resource group if missing” and add.
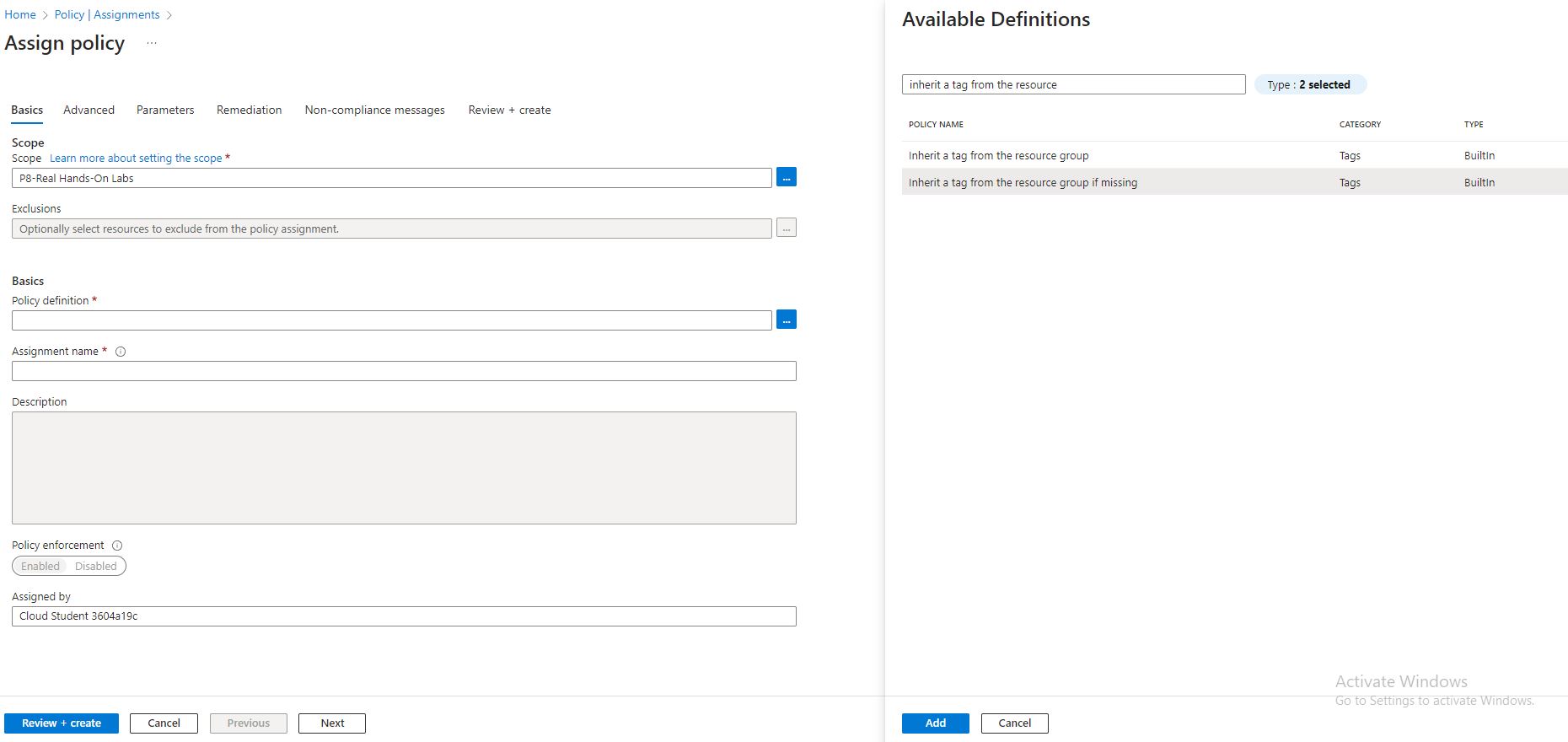
Skipped the advanced again and move to parameters and use the same tag name as earlier” Money Allocation”
Under remediation, I did not create any remediation yet, will come back to it, but on managed identity, the exiting resources may not be complaint (the existing VNet and MI). Here I selected the User assigned managed identity over the default system managed identity which I do not have the privileged and as in the real world which might result in the policy failing, hence I selected the user assigned managed identity.
Under scope I selected my subscription and lab resource groups and my existing managed identity, then review and create.
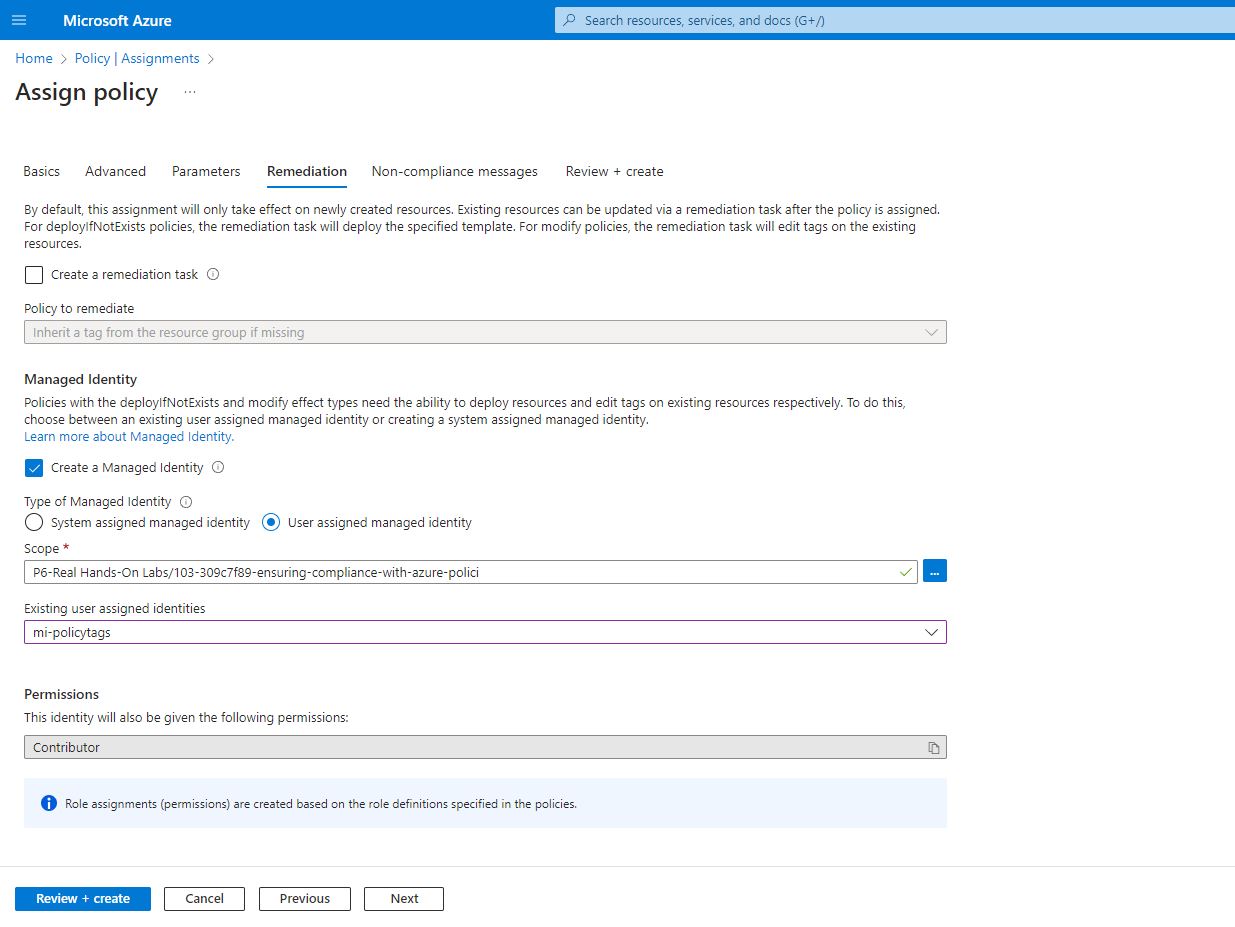
Now the next step is to create and update the existing resources.
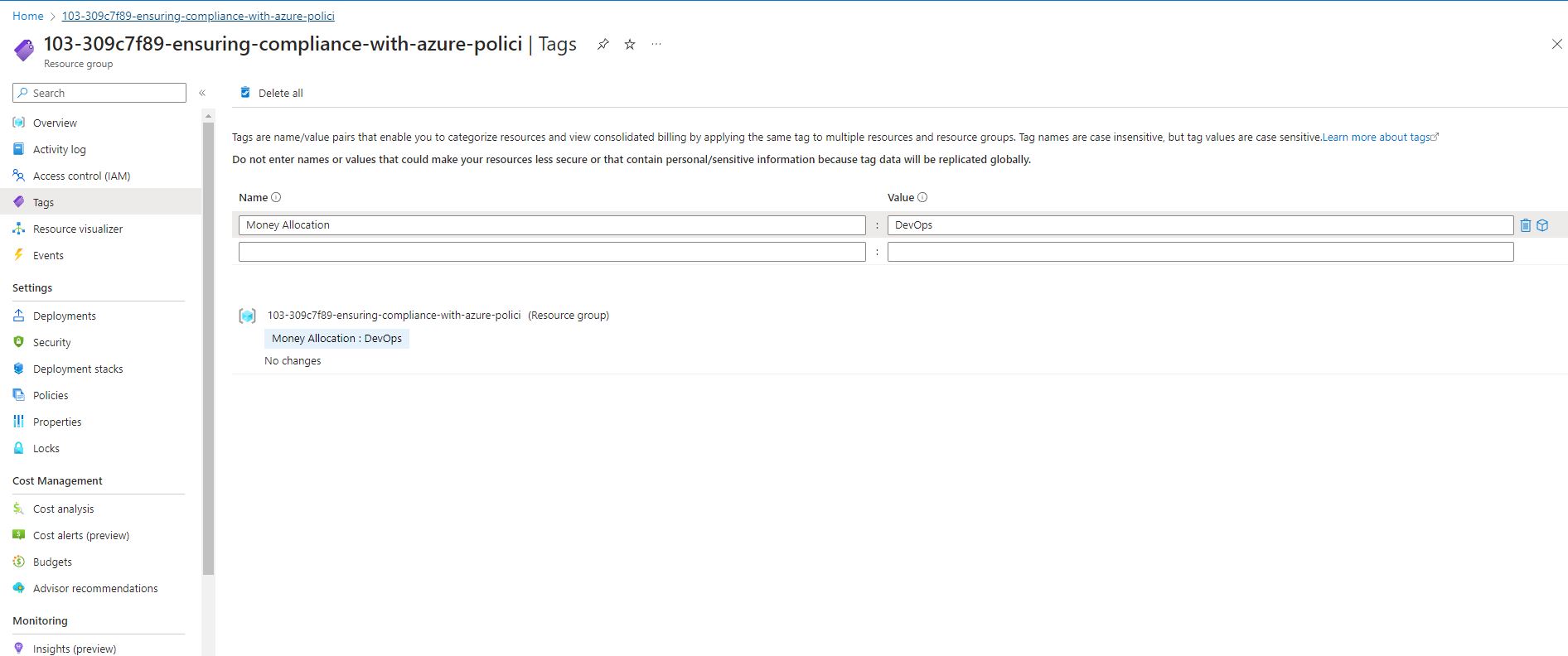
The first i updated the money Allocation tag on the resource group
From the portal home, navigated into the resource group, clicked on Tags and name the tag Money Allocation and the value= DevOps an then apply.
Now created a non-compliance resource. Go back to my resource group, make a note of my region (East US)
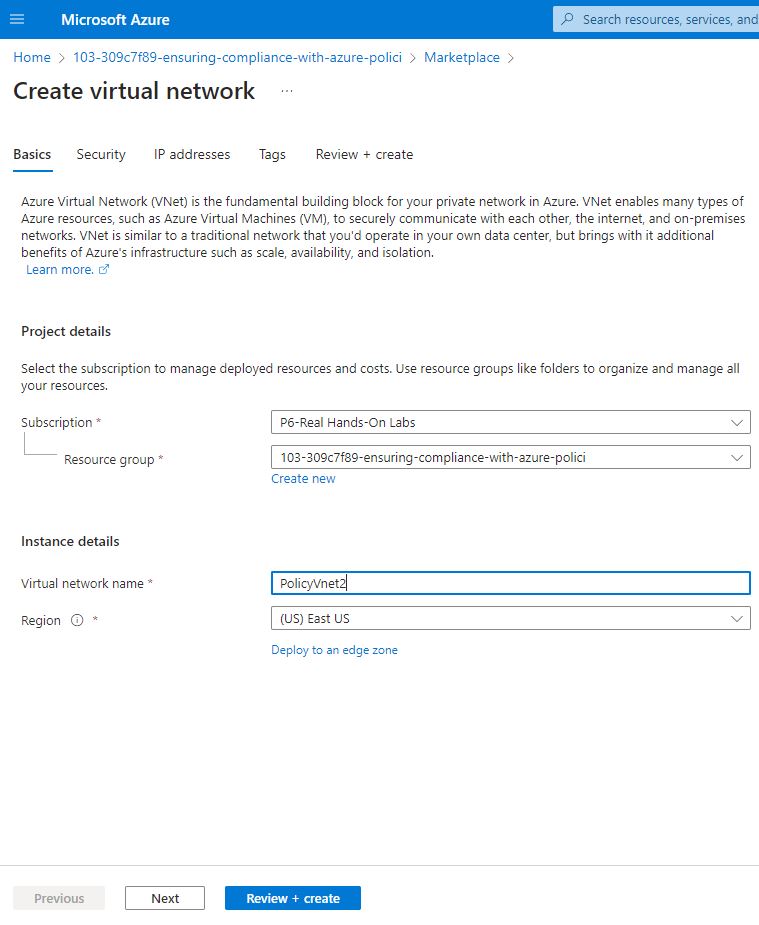
Then created a new virtual network.
Clicked on create, then select virtual network. And set the name to PolicyVnet2, also making sure it’s on the same region as my existing resources. No need to change anything else. Not including tags as I wanted to see the effect of the Azure policy. Then moved to review and create.
Once the deployment completed, I had to check the result of the policy assignment.
- Navigated back to the resource group
- Selected policyVnet2 I created last
- Checked the tags and confirm that the policyVnet2 has a Money Allocation tag: DevOps which Azure policy has applied by inheriting it from the resource group.
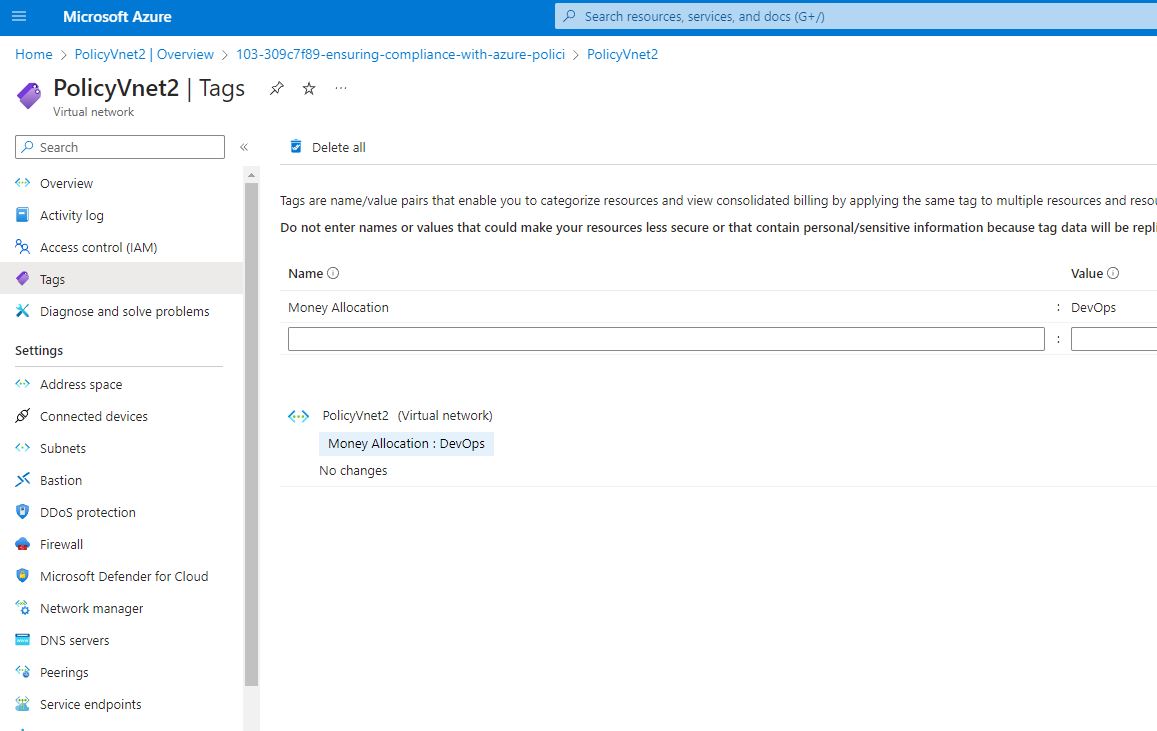
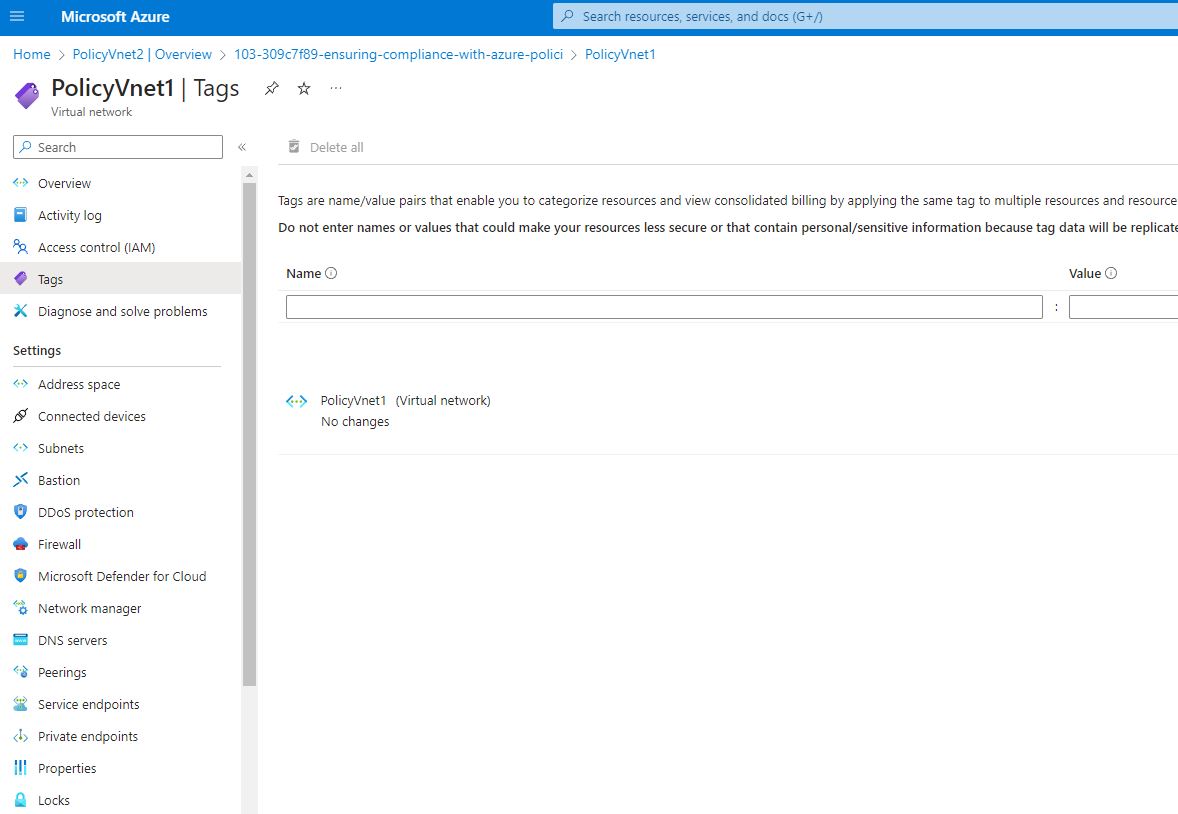
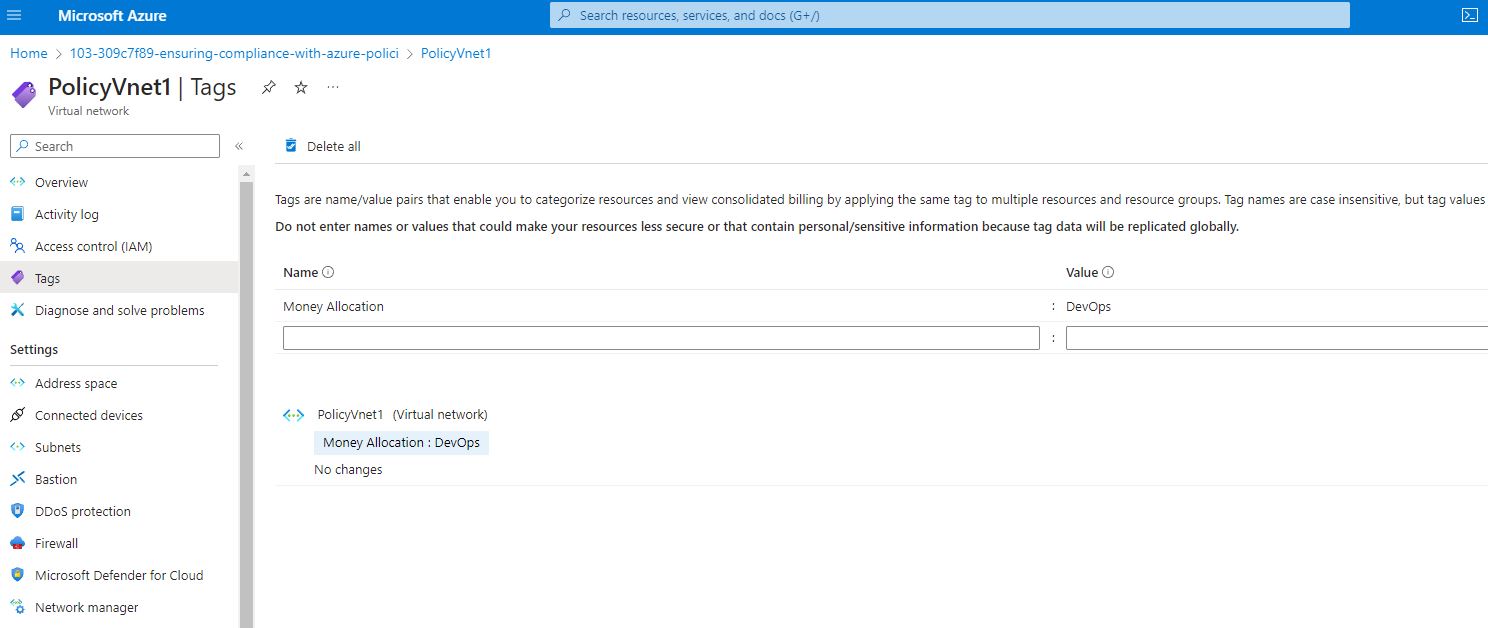
When I go back to the resource group and and select the policyVnet1, click on tags, I noticed that the PolicyyVnet1 still have no tags assigned.
To remediate the existing resources.
- I created the remediation tag.
- Searched for “policy” service again
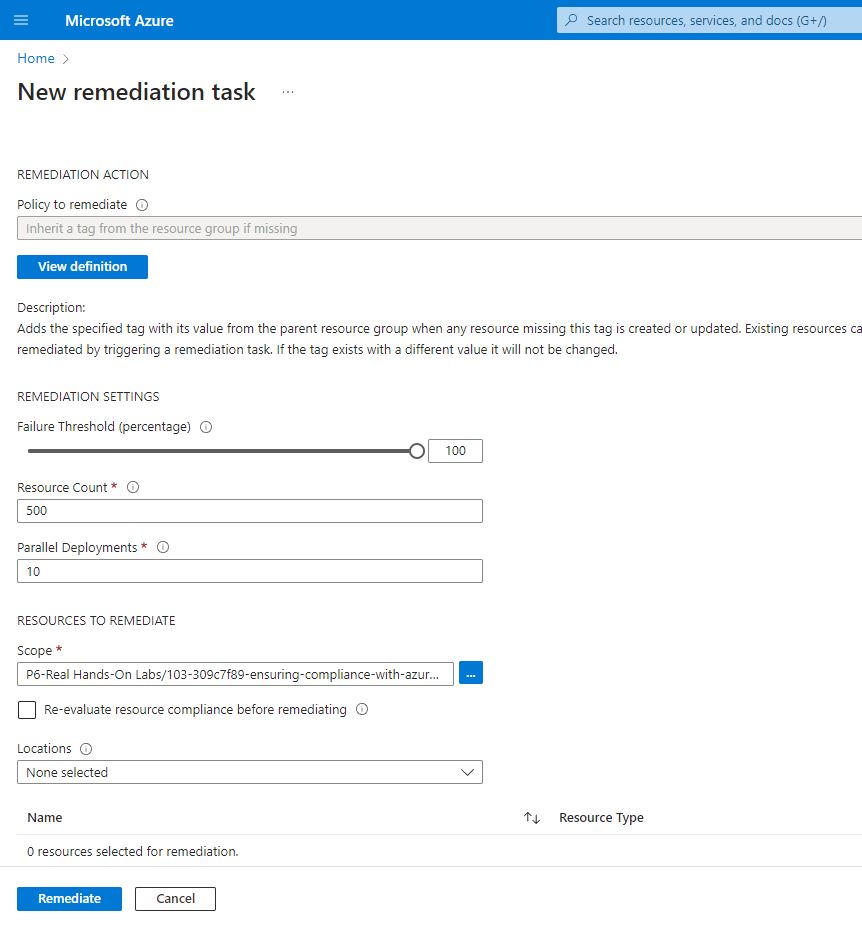
- On the left hand side, I selected remediation, changed my scope to my lab resource group.
- I choose policy definition “inherit tag from the resource group if missing”
- On the remediation action page: Selected my lab resource group from the scope.
Unfortunately I couldn’t see my resources.
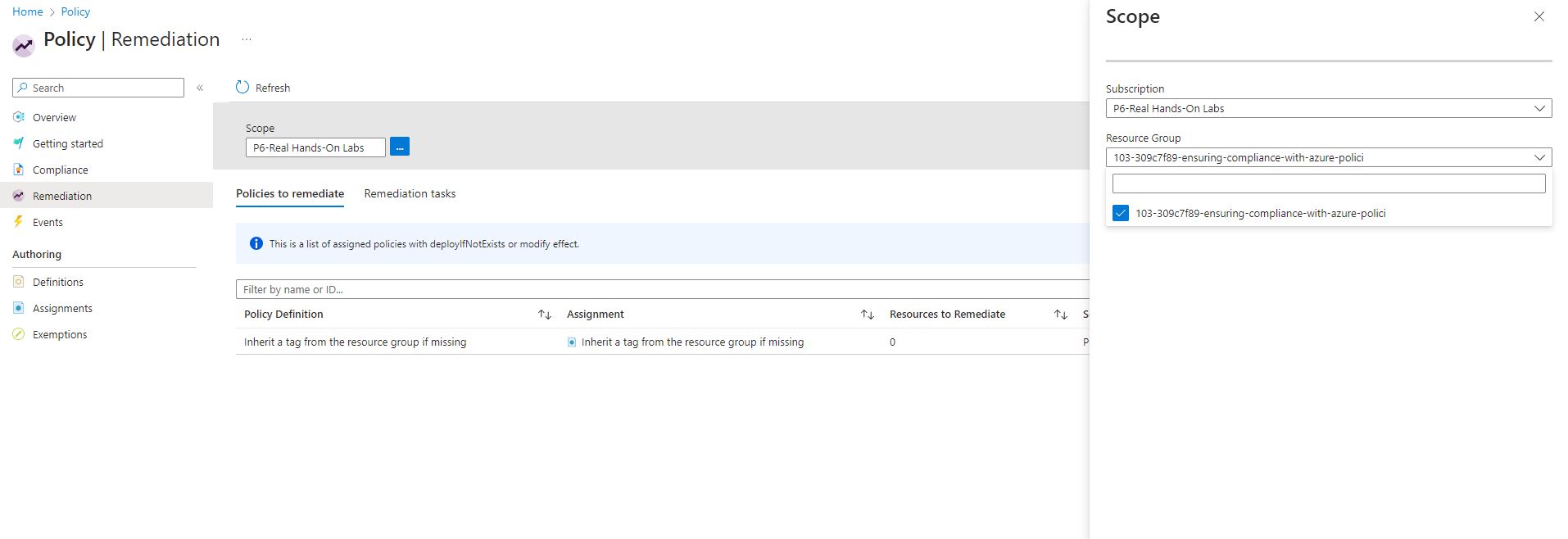
I couldn’t see my resources, I had to tick the Re-evaluate resource compliance before remediating and select my region. East US.
Once the remediation has completed, I now check the virtual network (policyVnet1). from tags I could see that the remediation tag has inherited the Money allocation tag from the resource group to this virtual network.
In today’s cloud-driven landscape, ensuring compliance and governance in Azure is paramount. Azure Policies is a powerful tool for maintaining security, cost control, and adherence to organizational standards in your Azure environment.
If you find this interesting, follow for more.