Application rules within Azure Firewall enable you to create fine-grained policies that allow or deny traffic based on application-specific criteria, such as URLs, domains, or HTTP methods.
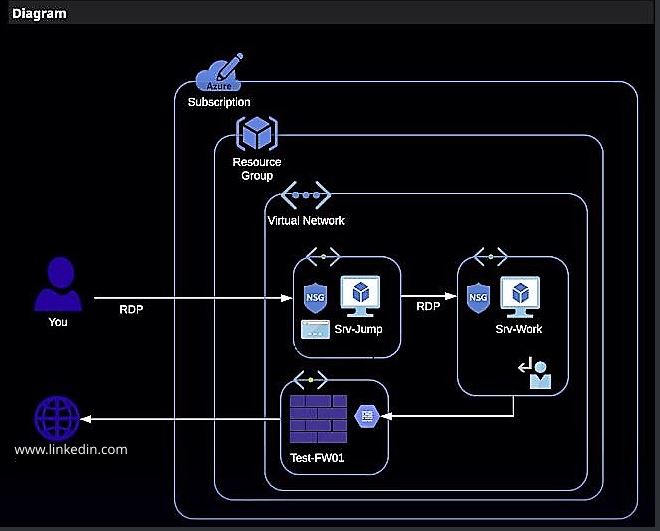
In this lab, i was able to configure an Azure firewall Application Rule to allow access through a firewall to www.linkedin.com from a VM on a private subnet in Azure, following the scenario below.
Pavic homes Limited has deployed a secure multi-server architecture in Azure. This consists of a jump server and a work server. The jump server can be reached from the Internet with remote desktop. The work server cannot be reached from the Internet. The work server can also not access the Internet, as the subnet on which it is located is configured to forward all traffic to an Azure Firewall which blocks that access. But it is now identified that access to several websites are required by the work server. To allow this, there is need to add a rule to the firewall to allow access to those sites. Here i will enable access to www.linkedin.com from the work server, configure this rule in the firewall, as shown below.
Okay, lets get started!
Log in to the Azure Portal with my lab credentials and access resources and srv-jump to get the ip address
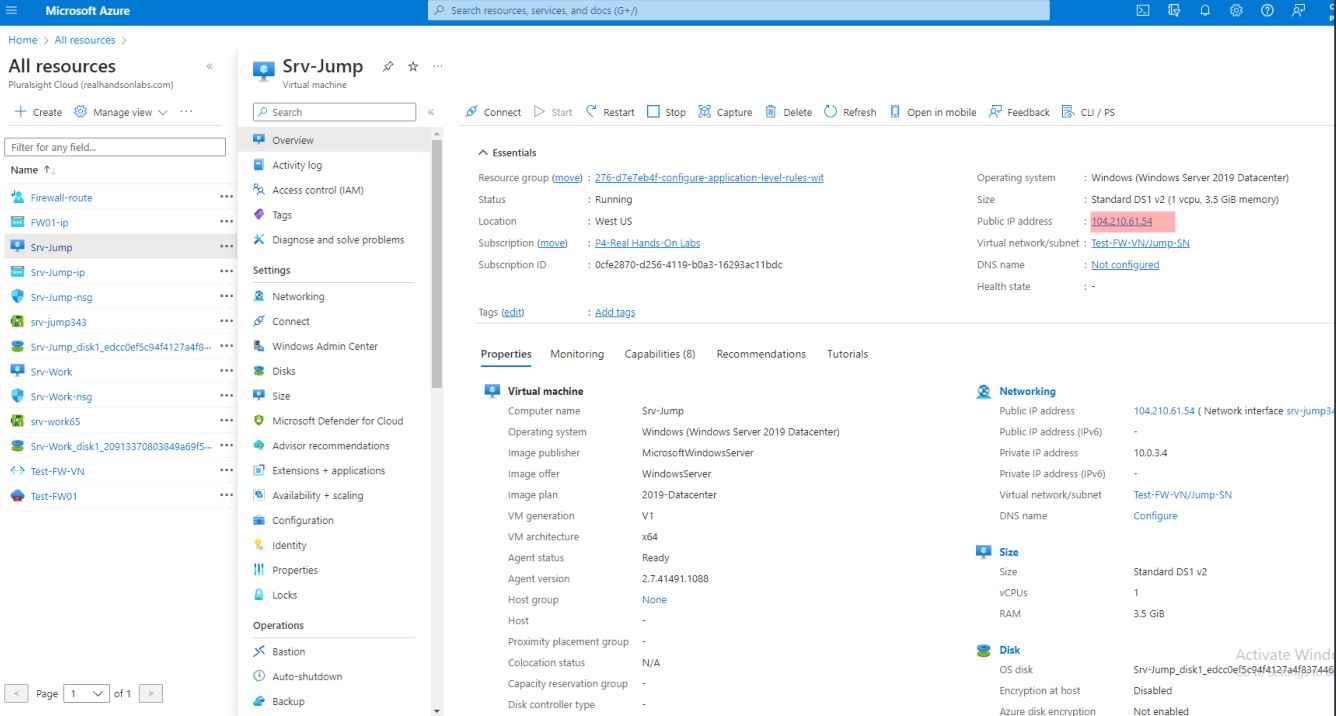
Remote into the Jump VM
Remote into the Work VM from the Jump VM (with my lab subscription credentials)
From the Srv-Jump, remote into Srv-Work using Remote Desktop. Use the credentials for the Srv-work server
Open Internet Explorer.
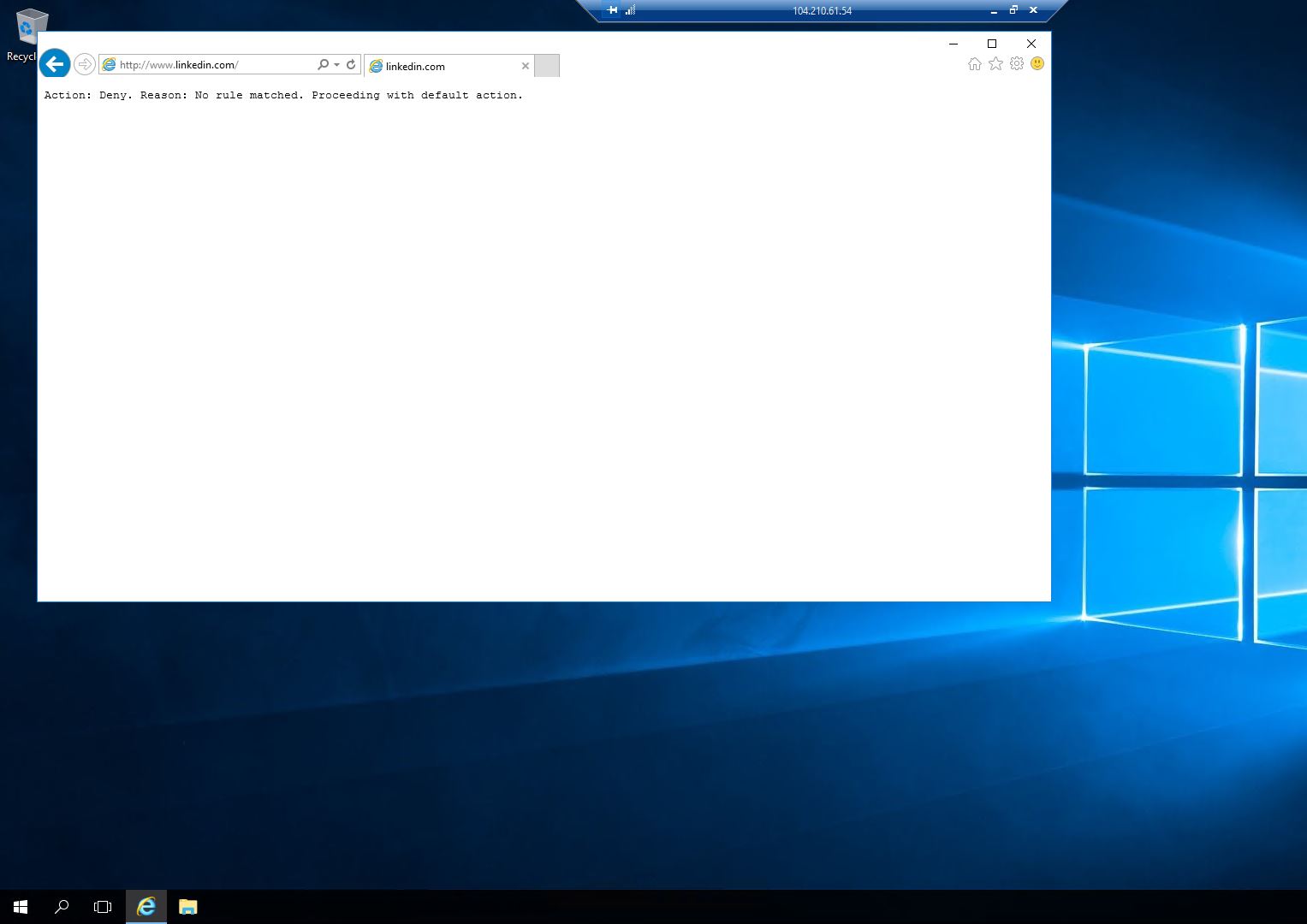
Entered www.linkedin.com in the address bar and press enter.
The browser will displayed a message that access to the site is denied.
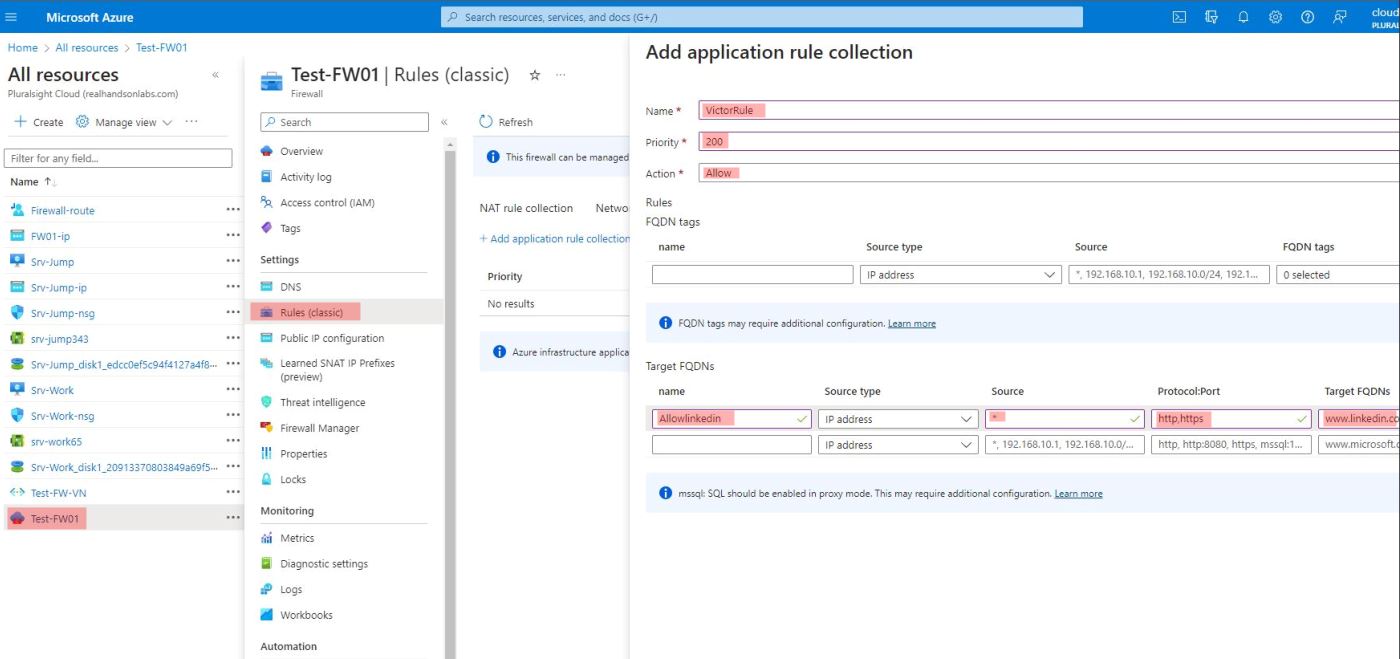
Configured the Firewall Rule to Allow Access to www.linkedin.com from the Work VM
In the Azure Portal, navigate to the resource TEST-FW01. In the Settings section of the menu, click Rules. On the page that appears, click Application rule collection, and then + Add application rule collection.
Entered the following into the form: Name: MyRule Priority: 200 (Priority: The order in which the rule is evaluated. Rules with lower numbers are evaluated first)
In the Target FQDNs section, enter: Name: AllowLinkedin Source: * Protocol:Port: http,https Target FQDNs: www.linkedin.com
Then press the Add button.
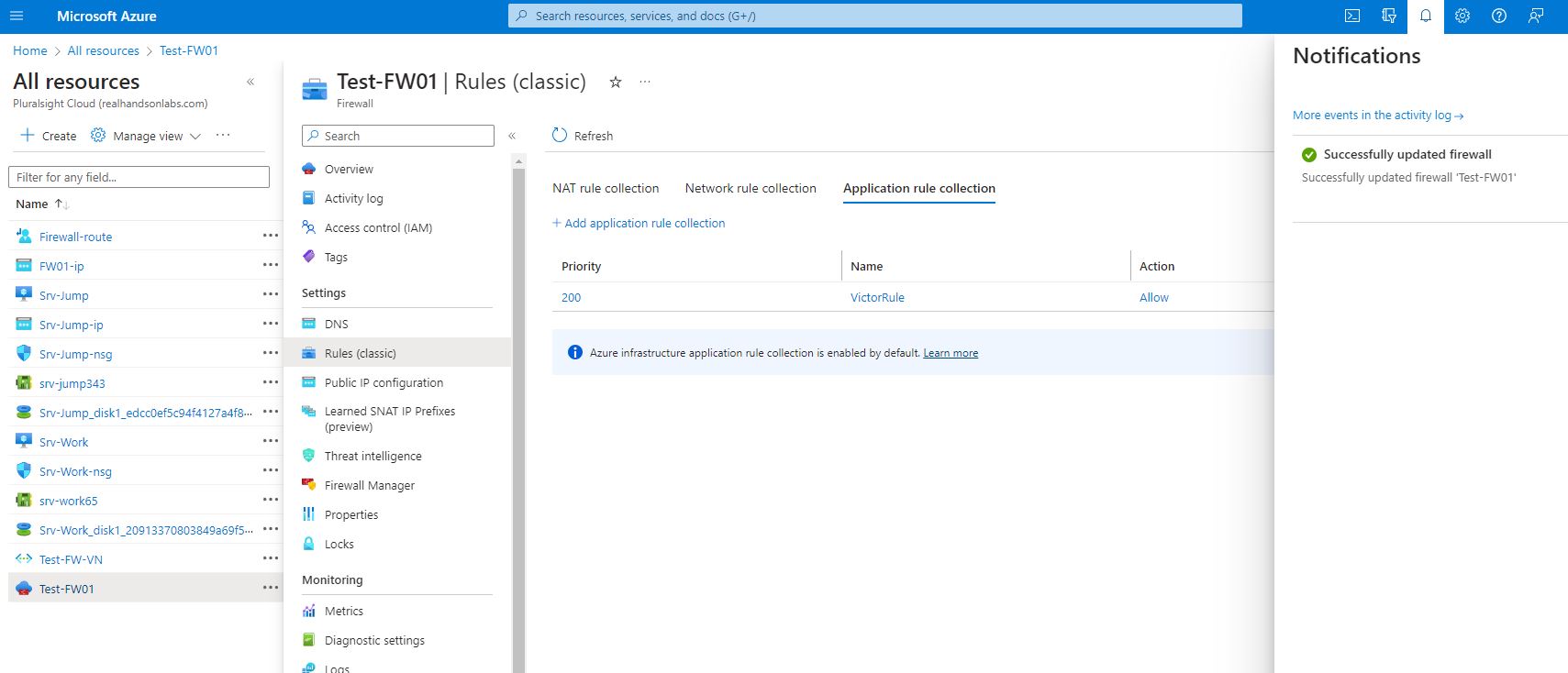
From Notification icon, confirm if the update was successful.
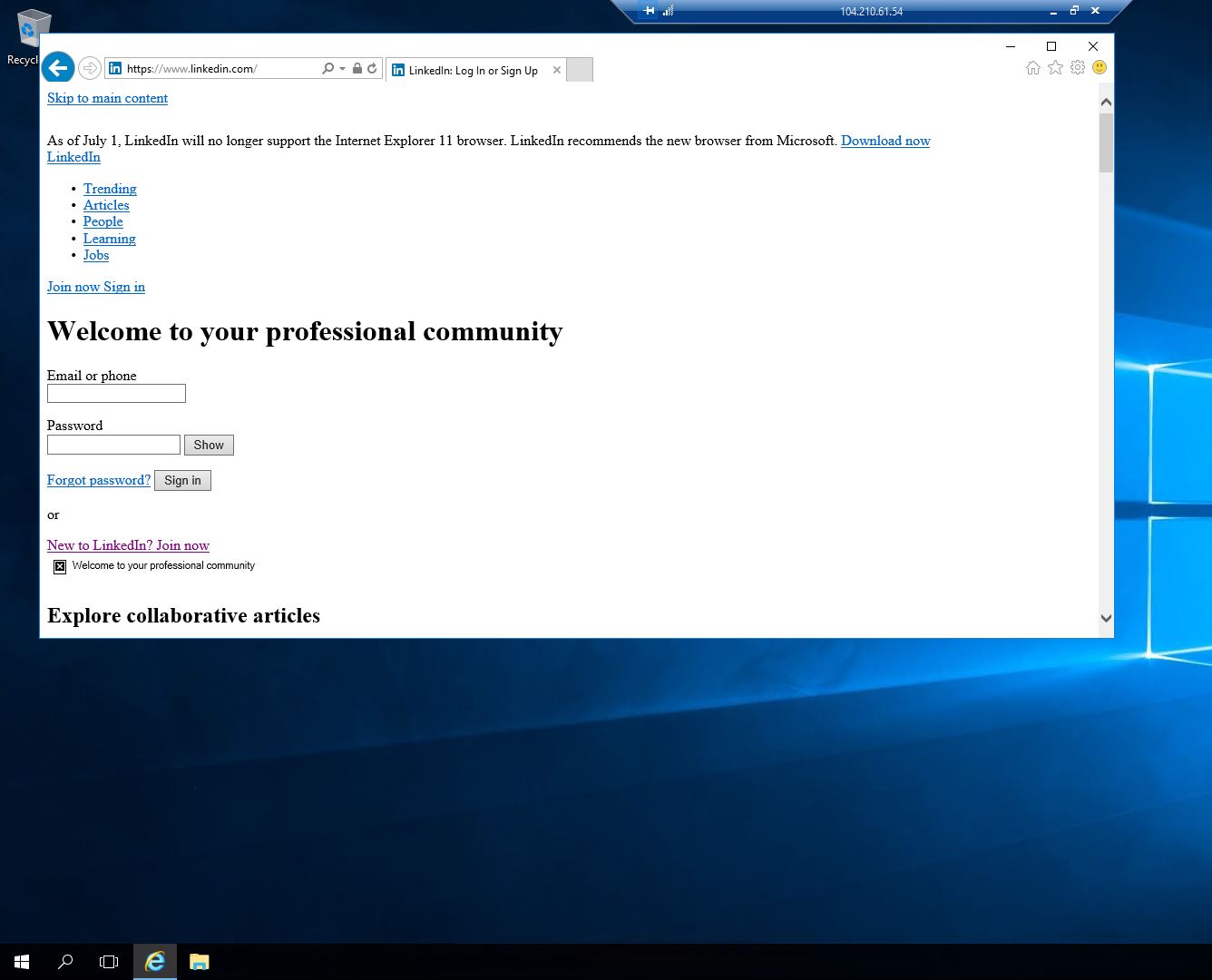
Retry Opening www.linkedin.com from the Work VM
In the browser on the Work VM, refreshed the page for www.linkedin.com. We can now access the site, although we’ll get a lot of questions from Internet Explorer about allowing access and content being blocked. That’s ok. It’s a response to finally being allowed through the firewall.
After configuring application rules, it’s important to monitor traffic and perform troubleshooting as needed. Azure Firewall provides logging and monitoring capabilities that can help you analyze and diagnose traffic patterns.
Thank you for joining me on this project. Look out for my next project.
